THIRD-PARTY RISK MANAGEMENT STANDARD OPERATING PROCEDURE
TABLE OF CONTENTS
- Purpose and Scope
- Definitions and Tiering Criteria
- Lifecycle Overview
3.1 Intake and Criticality Scoring
3.2 Tiering Decision
3.3 Due Diligence and Evidence Collection
3.4 Contracting Controls
3.5 Onboarding
3.6 Ongoing Monitoring
3.7 Periodic Reassessment
3.8 Offboarding and Data Return/Deletion - Roles and RACI
- Documentation and Systems of Record
- Metrics, KRIs, and Reporting
- Exceptions and Compensating Controls
- Review Cadence and Ownership
- Annexes (Checklists, Templates)
- California-Specific Requirements
1. PURPOSE AND SCOPE
- Standardize third-party risk management (TPRM) for vendors, partners, and subprocessors.
- Applies to all third parties that access company data, systems, customers, or critical operations.
2. DEFINITIONS AND TIERING CRITERIA
- Tiers: Critical, High, Medium, Low.
- Criteria: data sensitivity (PII/PHI/PCI/IP), system connectivity, transaction volume, operational reliance, regulatory impact, geographic risk, public official exposure.
- Tier drives diligence depth, approval levels, and monitoring cadence.
3. LIFECYCLE OVERVIEW
3.1 Intake and Criticality Scoring
- Business owner submits intake with use case, data types, integrations, geos, and alternatives considered.
- Initial risk score auto-calculated; Compliance/Security review for accuracy.
3.2 Tiering Decision
- Assign tier based on scoring and professional judgment; document rationale.
- Escalate ambiguous cases to Compliance/Security leadership.
3.3 Due Diligence and Evidence Collection
- Issue questionnaire aligned to tier; collect artifacts (policies, SOC/ISO/PCI, pen test summaries, insurance, subprocessor list, DPIA if applicable).
- Perform sanctions/PEP/adverse media screening; export controls checks where relevant.
- Evaluate privacy (DSR handling, transfers), security (access, encryption, logging, SDLC), resilience (BC/DR), and legal (licenses, regulatory history).
3.4 Contracting Controls
- Required terms by tier: DPA + SCC/IDTA (if needed), security addendum, uptime/SLA, breach notice timelines, audit/pen test rights, subcontractor approvals, IP/confidentiality, indemnities, insurance, termination, and data return/deletion.
- Deviations require approvals and compensating controls recorded.
3.5 Onboarding
- Validate controls implemented; system access provisioned least-privilege; logging enabled; owners assigned; repositories updated.
3.6 Ongoing Monitoring
- Track incidents, complaints, SLA performance, change notices (scope, subprocessors, location), and financial viability.
- Require timely notice of security/privacy incidents and material changes.
3.7 Periodic Reassessment
- Cadence by tier (e.g., Critical: annual; High: 18 months; Medium: 24 months; Low: 36 months).
- Triggered reassessment upon incidents, scope changes, new data types/geos, M&A, or regulatory changes.
3.8 Offboarding and Data Return/Deletion
- Confirm data return/deletion; revoke access; collect certifications; migrate services if needed; close out records in TPRM system.
4. ROLES AND RACI
- Business Owner: initiates intake, funds vendor, owns performance, ensures adherence.
- Compliance: policy oversight, sanctions/export review, contract clauses, exceptions.
- Security: technical review, security clauses, monitoring requirements.
- Privacy: data mapping, DPA/SCCs, transfer risk, DSR process.
- Procurement/Legal: commercial/legal terms, signature.
- Finance: payment controls.
- Internal Audit: independent review/testing (if applicable).
- RACI table: [INSERT MATRIX BY ACTIVITY].
5. DOCUMENTATION AND SYSTEMS OF RECORD
- Central TPRM system/ticket stores intake, tiering, approvals, questionnaires, evidence, exceptions, contracts, monitoring notes, and reassessments.
- Version control for artifacts; link to contract repository.
6. METRICS, KRIs, AND REPORTING
- Time-to-approve by tier; exception count/aging; reassessment completion rate; incident notifications; SLA breaches; critical vendor concentration.
- Report to [BOARD/COMMITTEE/EXCO] on cadence [QUARTERLY].
7. EXCEPTIONS AND COMPENSATING CONTROLS
- Document exceptions with risk owner, approver, expiration/review date, and compensating controls; track to closure.
8. REVIEW CADENCE AND OWNERSHIP
- Owner: [COMPLIANCE/SECURITY/PROCUREMENT].
- Review SOP annually or upon material change (new regulation, major incident, program redesign).
9. ANNEXES (EXAMPLES)
- Annex A: Intake form fields.
- Annex B: Tiering criteria and scoring model.
- Annex C: Required clauses checklist by tier.
- Annex D: Reassessment checklist and evidence list.
10. CALIFORNIA-SPECIFIC REQUIREMENTS
- CPRA service provider/contractor terms required in vendor agreements, including restrictions on use, retention, and disclosure.
- Vendor support for CPRA consumer requests and audit rights must be documented in the DPA and onboarding checklist.
- For vendors processing sensitive personal information, confirm data minimization, purpose limitation, and opt-out/limit mechanisms.
- Apply California breach notification requirements and timelines in incident response playbooks and vendor SLAs.
Do more with Ezel
This free template is just the beginning. See how Ezel helps legal teams draft, research, and collaborate faster.
AI that drafts while you watch
Tell the AI what you need and watch your document transform in real-time. No more copy-pasting between tools or manually formatting changes.
- Natural language commands: "Add a force majeure clause"
- Context-aware suggestions based on document type
- Real-time streaming shows edits as they happen
- Milestone tracking and version comparison
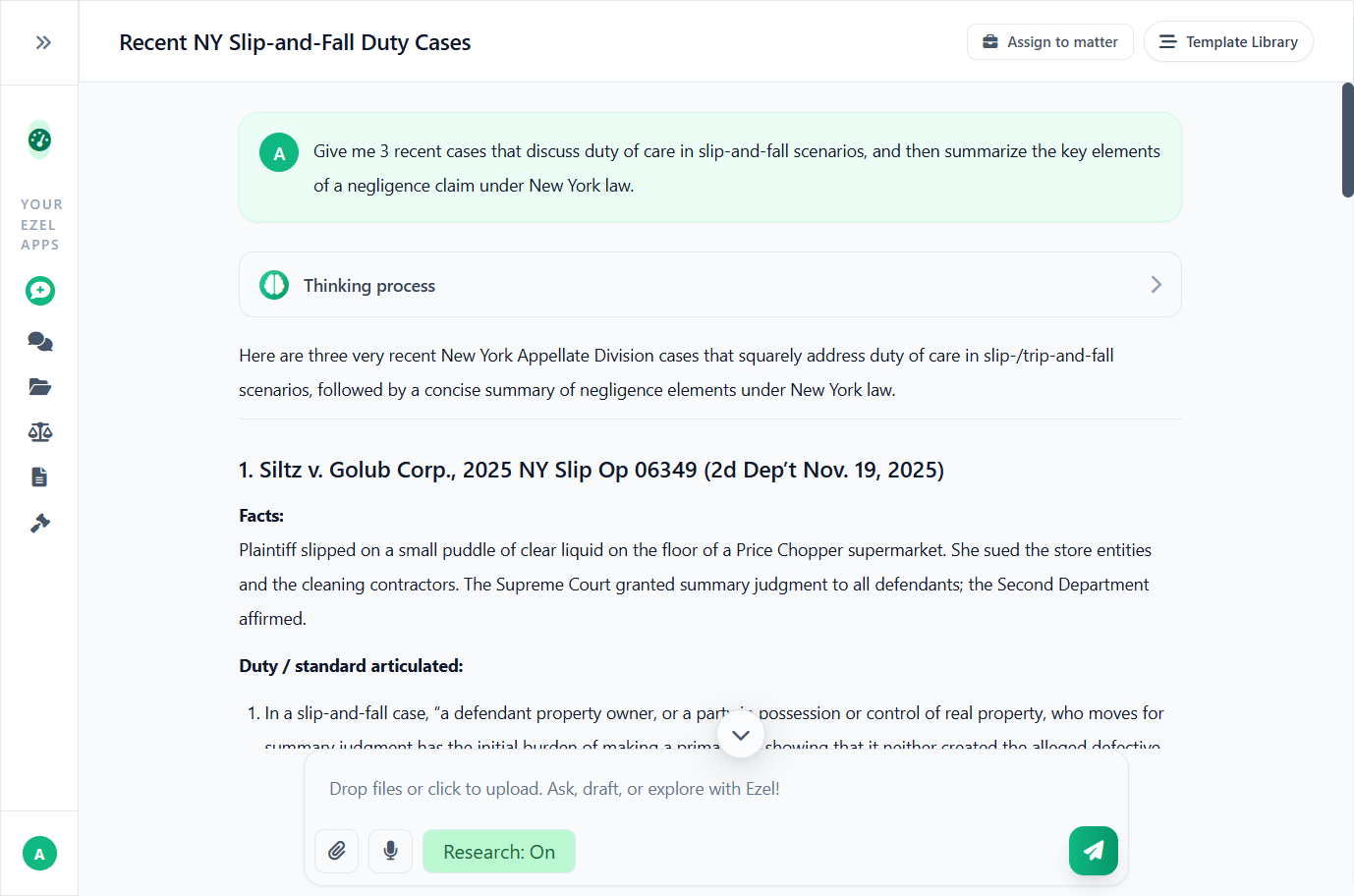
Research and draft in one conversation
Ask questions, attach documents, and get answers grounded in case law. Link chats to matters so the AI remembers your context.
- Pull statutes, case law, and secondary sources
- Attach and analyze contracts mid-conversation
- Link chats to matters for automatic context
- Your data never trains AI models
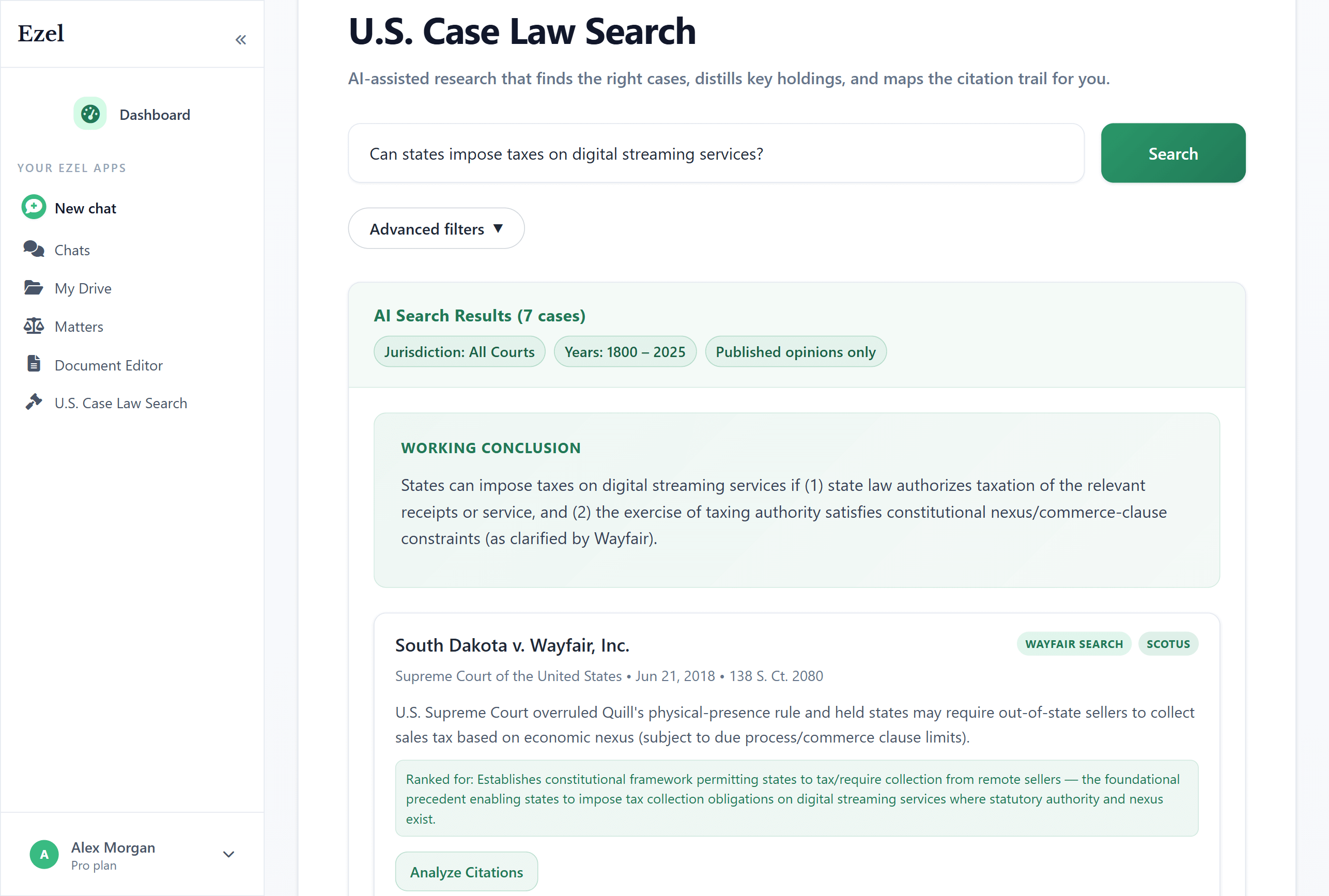
Search like you think
Describe your legal question in plain English. Filter by jurisdiction, date, and court level. Read full opinions without leaving Ezel.
- All 50 states plus federal courts
- Natural language queries - no boolean syntax
- Citation analysis and network exploration
- Copy quotes with automatic citation generation
Ready to transform your legal workflow?
Join legal teams using Ezel to draft documents, research case law, and organize matters — all in one workspace.