SECURITY ADDENDUM (ENTERPRISE SAAS)
New York Jurisdictional Version
TABLE OF CONTENTS
- Scope and Order of Precedence
- Security Program
- Access Controls and Authentication
- Encryption
- Network and Infrastructure Security
- Application Security and SDLC
- Vulnerability Management
- Logging and Monitoring
- Business Continuity and Disaster Recovery
- Data Segregation and Residency
- Penetration Testing and Assessments
- Incident Response and Notification
- Audit and Compliance Reports
- Third-Party Subprocessors
- Physical Security
- Personnel Security and Training
- Data Return and Deletion
- Changes to Security Controls
- New York-Specific Data Protection Requirements
- Governing Law and Dispute Resolution
1. SCOPE AND ORDER OF PRECEDENCE
- Applies to the Services under the [SaaS Agreement name/date].
- If conflict with the SaaS Agreement/DPA on security matters, this Addendum governs; otherwise, SaaS Agreement controls.
2. SECURITY PROGRAM
- Provider maintains a written information security program with administrative, technical, and physical safeguards appropriate to risk, aligned to [ISO 27001/SOC 2/other].
- Provider's security program shall comply with the New York Stop Hacks and Improve Electronic Data Security Act (SHIELD Act), N.Y. Gen. Bus. Law sections 899-aa and 899-bb, requiring reasonable safeguards to protect the security, confidentiality, and integrity of private information.
- Provider shall implement a data security program that includes: (i) reasonable administrative safeguards; (ii) reasonable technical safeguards; and (iii) reasonable physical safeguards, consistent with the SHIELD Act requirements.
3. ACCESS CONTROLS AND AUTHENTICATION
- Role-based access; least privilege; MFA for administrative access; strong password/secret policies; session management; timely deprovisioning.
4. ENCRYPTION
- In transit: TLS [1.2/1.3] or better; at rest: industry-standard encryption for Customer Data stores.
- Key management: [KMS/HSM], separation of duties, rotation policies.
5. NETWORK AND INFRASTRUCTURE SECURITY
- Segmentation of environments (prod/non-prod); firewalls/security groups; DDoS protections; hardened images; configuration management and baselines.
6. APPLICATION SECURITY AND SDLC
- Secure development lifecycle with code review, dependency scanning, SAST/DAST for relevant components; change management with approvals and rollback plans.
7. VULNERABILITY MANAGEMENT
- Regular scanning; prioritization/remediation targets:
- Critical: [X] hours/days; High: [Y] days; Medium: [Z] days; Low: [define].
- Patch management process; emergency patching for exploited vulnerabilities.
8. LOGGING AND MONITORING
- Centralized logging for auth, access, admin actions, and security events; time-synchronized; retention [X] days/months; alerting for anomalous events.
9. BUSINESS CONTINUITY AND DISASTER RECOVERY
- Documented BC/DR plan; tested [annually/semi-annually]; RPO [X hours], RTO [Y hours]; backups encrypted and tested for restoration.
10. DATA SEGREGATION AND RESIDENCY
- Logical/tenant isolation; data residency options [Regions] if offered; no relocation without notice and updated transfer mechanisms.
11. PENETRATION TESTING AND ASSESSMENTS
- Independent penetration tests [annually/semi-annually]; summary reports available under NDA; remediation tracked to closure.
- Customer-sourced testing requires prior written approval and coordinated scope.
12. INCIDENT RESPONSE AND NOTIFICATION
- Incident response plan with roles, runbooks, and communications.
- Notification to Customer without undue delay and within [X] hours of confirming a Security Incident affecting Customer Data; include nature, scope, mitigations, and recommended actions.
- In compliance with N.Y. Gen. Bus. Law section 899-aa (as amended by SHIELD Act), Provider shall notify Customer of any breach of the security of the system following discovery or notification of the breach in the most expedient time possible and without unreasonable delay, consistent with the legitimate needs of law enforcement and any measures necessary to determine the scope of the breach and restore the reasonable integrity of the system.
- Notification shall include: (i) contact information for Provider; (ii) description of the categories of information reasonably believed to have been accessed or acquired; and (iii) dates, estimated dates, or date ranges of the security breach.
- Post-incident report for material incidents within [Y] business days.
13. AUDIT AND COMPLIANCE REPORTS
- Provide current SOC 2 / ISO 27001 certificate and summary upon request; significant exceptions disclosed with remediation plans.
- Onsite/customer audits: [once per year] with reasonable notice; subject to confidentiality and limited to security controls; time/materials fees if onsite.
14. THIRD-PARTY SUBPROCESSORS
- Subprocessors must meet equivalent security standards; list available at [URL/Annex]; notice of new subprocessors with [X] days to object on reasonable grounds; Provider remains liable.
- Subprocessors must implement reasonable safeguards consistent with SHIELD Act requirements for the protection of private information.
15. PHYSICAL SECURITY
- Data centers with industry-standard controls: access badges/biometrics, CCTV, visitor logging, environmental controls, and redundant power/cooling.
16. PERSONNEL SECURITY AND TRAINING
- Background checks where lawful for personnel with Customer Data access, subject to New York Correction Law Article 23-A and any applicable local fair chance hiring laws; confidentiality agreements; security and privacy training at onboarding and [annual] refreshers.
17. DATA RETURN AND DELETION
- Upon termination/expiry, Customer Data returned or deleted per Agreement/DPA within [X] days; secure deletion methods; backups aged out on standard cycles unless legal hold applies.
- Data disposal shall comply with N.Y. Gen. Bus. Law section 399-H requirements for proper disposal of records containing personal identifying information.
18. CHANGES TO SECURITY CONTROLS
- Material reductions not permitted without Customer consent; non-material updates allowed to improve or maintain security posture.
- Notice of material changes to contact [security contact].
19. NEW YORK-SPECIFIC DATA PROTECTION REQUIREMENTS
19.1 SHIELD Act Compliance
- Provider shall maintain a data security program that includes the following elements as required by the SHIELD Act:
- Administrative safeguards including: designating personnel responsible for security; identifying reasonably foreseeable risks; assessing safeguard sufficiency; training and management of security program; selecting and retaining service providers capable of maintaining appropriate safeguards;
- Technical safeguards including: assessing risks in network and software design; assessing risks in information processing, transmission, and storage; detecting, preventing, and responding to intrusions; and regular testing and monitoring of controls;
- Physical safeguards including: assessing risks of information storage and disposal; detecting, preventing, and responding to intrusions; protecting against unauthorized access during or after collection, transportation, and destruction; and disposal of private information in a manner designed to protect against unauthorized access.
19.2 New York Trade Secret Protection
- Provider acknowledges that Customer's Confidential Information may include trade secrets as protected under New York common law and the federal Defend Trade Secrets Act (18 U.S.C. section 1836 et seq.), and shall protect such information accordingly.
19.3 New York E-Signatures
- Electronic signatures under this Addendum shall be valid and enforceable pursuant to the New York Electronic Signatures and Records Act (N.Y. State Tech. Law Article 3) and the federal Electronic Signatures in Global and National Commerce Act (E-SIGN Act).
19.4 Financial Services Considerations
- If Customer is a covered entity under the New York Department of Financial Services Cybersecurity Regulation (23 NYCRR Part 500), Provider shall cooperate with Customer to ensure compliance with applicable third-party service provider requirements under 23 NYCRR section 500.11.
20. GOVERNING LAW AND DISPUTE RESOLUTION
20.1 Governing Law
This Addendum and any dispute arising out of or relating hereto shall be governed by and construed in accordance with the laws of the State of New York, without regard to its conflict of laws rules.
20.2 Forum Selection
Subject to any arbitration provisions in the Master Agreement, the Parties consent to the exclusive jurisdiction of the state and federal courts located in [New York County / Kings County / other New York County], New York, for any litigation arising out of or relating to this Addendum, and waive any objection to venue or forum non conveniens.
20.3 Jury Trial Waiver
EACH PARTY HEREBY KNOWINGLY, VOLUNTARILY, AND IRREVOCABLY WAIVES ITS RIGHT TO A TRIAL BY JURY IN ANY ACTION OR PROCEEDING ARISING OUT OF OR RELATING TO THIS ADDENDUM.
[// GUIDANCE: New York courts generally enforce contractual jury waivers between sophisticated commercial parties. Consider express acknowledgment language for additional enforceability.]
20.4 Injunctive Relief
Each Party acknowledges that a breach of the security obligations herein would cause irreparable harm for which monetary damages are an inadequate remedy. Accordingly, in the event of any such breach, the non-breaching Party may seek injunctive relief in addition to any other remedy available at law or equity, without posting bond or other security to the extent permitted under New York CPLR section 6312.
20.5 Late Payment Interest
Late payments under this Addendum shall accrue interest at the rate specified in the Master Agreement, or if not specified, at 9% per annum pursuant to N.Y. CPLR section 5004, or the maximum rate permitted under New York General Obligations Law sections 5-501 and 5-521 (16% per annum for most commercial transactions), whichever is applicable and agreed by the parties.
Do more with Ezel
This free template is just the beginning. See how Ezel helps legal teams draft, research, and collaborate faster.
AI that drafts while you watch
Tell the AI what you need and watch your document transform in real-time. No more copy-pasting between tools or manually formatting changes.
- Natural language commands: "Add a force majeure clause"
- Context-aware suggestions based on document type
- Real-time streaming shows edits as they happen
- Milestone tracking and version comparison
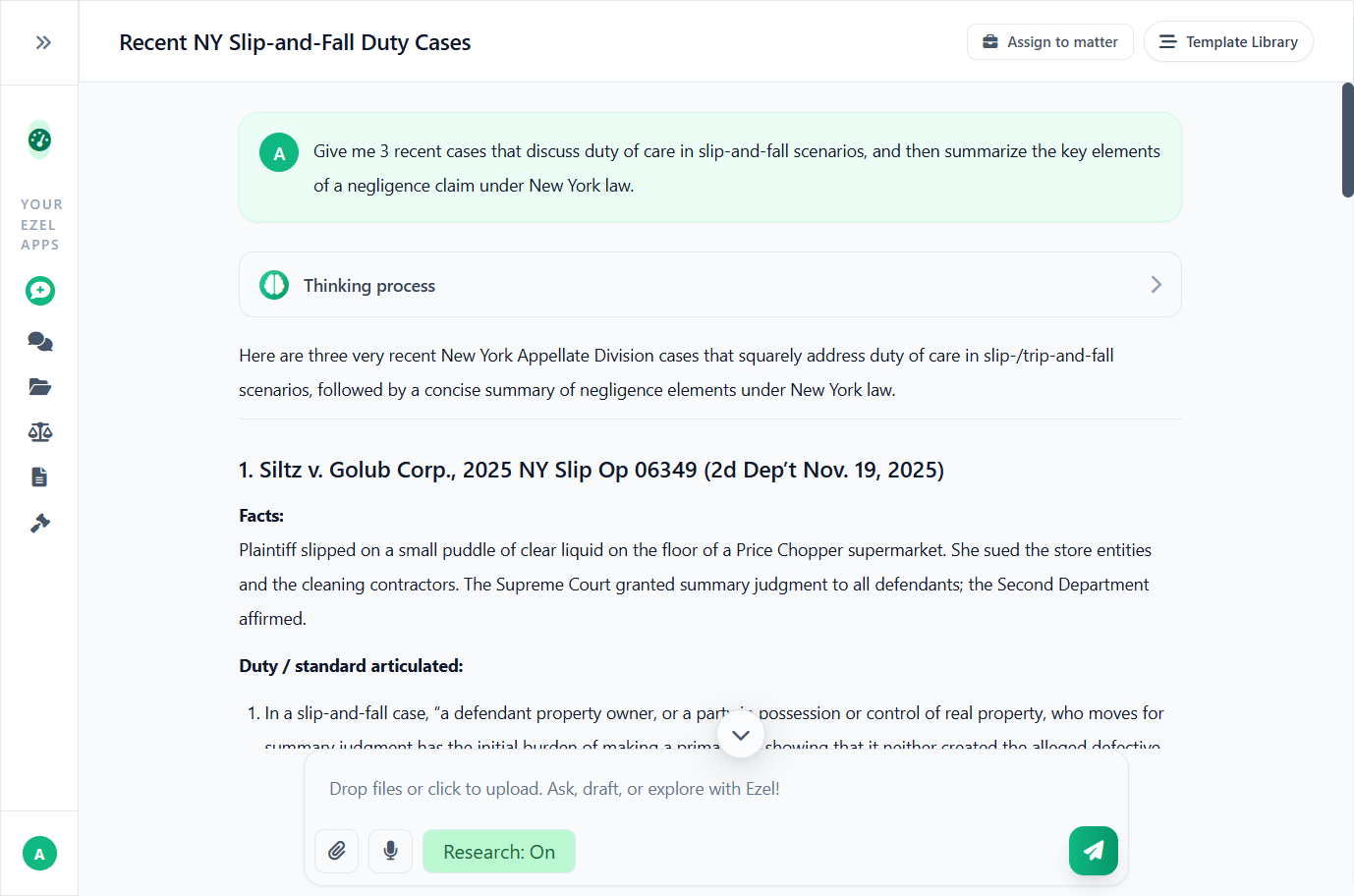
Research and draft in one conversation
Ask questions, attach documents, and get answers grounded in case law. Link chats to matters so the AI remembers your context.
- Pull statutes, case law, and secondary sources
- Attach and analyze contracts mid-conversation
- Link chats to matters for automatic context
- Your data never trains AI models
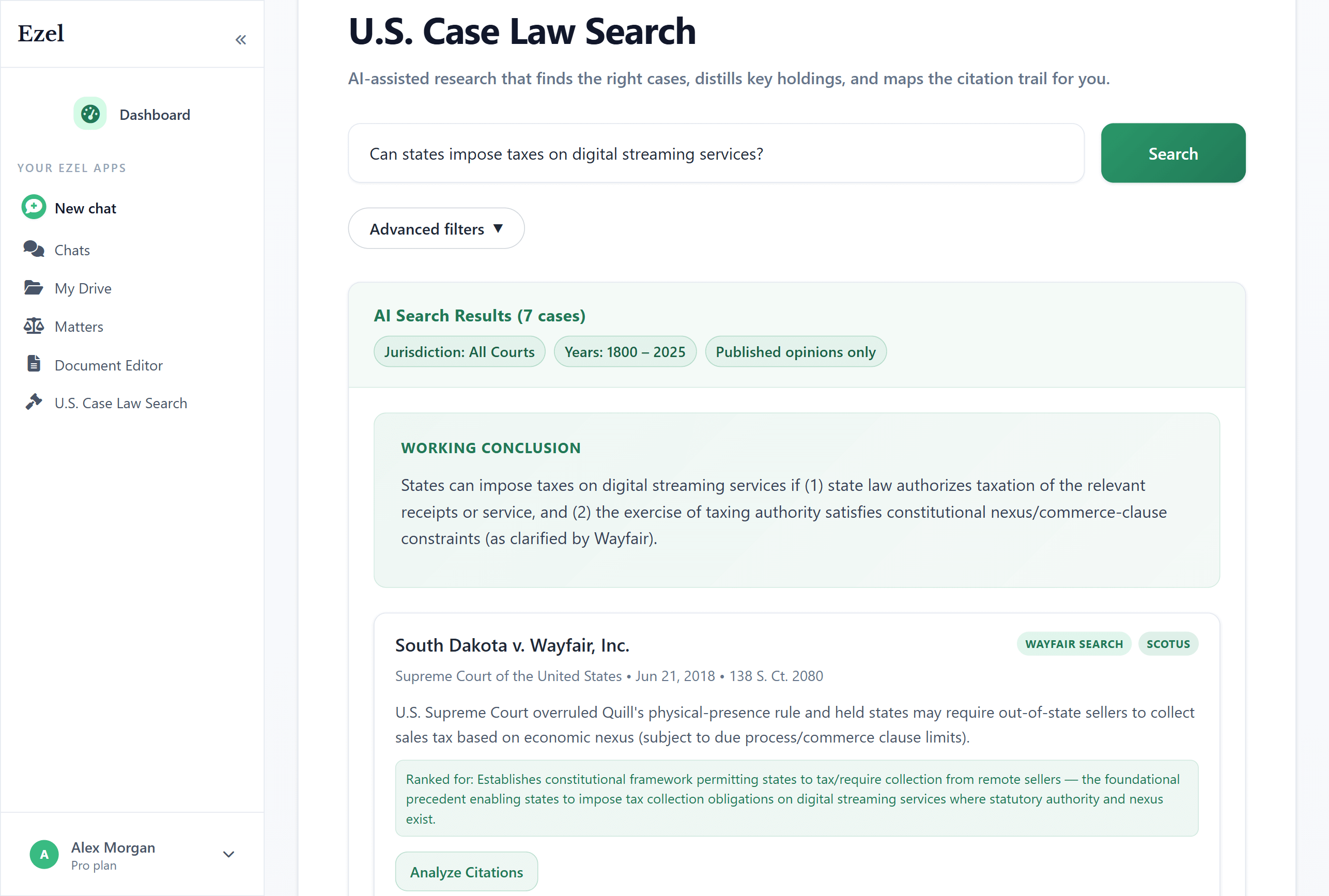
Search like you think
Describe your legal question in plain English. Filter by jurisdiction, date, and court level. Read full opinions without leaving Ezel.
- All 50 states plus federal courts
- Natural language queries - no boolean syntax
- Citation analysis and network exploration
- Copy quotes with automatic citation generation
Ready to transform your legal workflow?
Join legal teams using Ezel to draft documents, research case law, and organize matters — all in one workspace.