DATA PROTECTION IMPACT ASSESSMENT (DPIA)
(State overlay: WA)
1. Project Overview
- Project name/ID: [name]; owner: [business owner]; sponsor: [executive].
- Purpose and objectives: [describe].
- Timeline and launch date: [dates].
2. Scope of Processing
- Data subjects: [customers/employees/vendors/end users].
- Personal data categories: [contact, IDs, financial, location, biometric, health, minors].
- Sensitive data (state definition): [list per state law if applicable]; lawful basis/consent requirements: [insert].
- Volume and retention: [records/year], [retention schedule and deletion triggers].
- Processing activities: [collection, storage, analysis, sharing/sale/sharing status].
3. Legal Basis, Notices, and Rights
- No comprehensive consumer privacy law. Washington has breach notification statute only.
- Applicability: Persons/entities conducting business in WA owning/licensing PI of WA residents; state/local agencies.
- Consumer rights: No mandated access, correction, deletion, or opt-out rights (apply federal laws).
- Primary compliance obligation: Breach notification under RCW 19.255.010 (businesses) and RCW 42.56.590 (state/local agencies).
- Security standard: Reasonable security measures to protect PI.
4. Data Flow and Transfers
- Source systems: [list]; storage/hosting locations: [cloud region/data centers].
- Cross-border transfers: [EU/UK/other]; transfer tool: [SCCs/IDTA/CBPR if applicable].
- Recipients/vendors: [processors/subprocessors/controllers]; due diligence status and DPAs in place.
- Access controls: RBAC groups, least privilege, joiner/mover/leaver process.
5. Security and Controls
- Technical controls: encryption in transit/at rest [specify], key management, network segmentation, endpoint protections, logging/monitoring, DLP, backups, vulnerability management.
- Organizational controls: policies, training cadence, vendor due diligence, incident response playbook, change management.
- Authentication/authorization: [MFA/SAML/SSO]; session timeouts; privileged access reviews cadence.
6. Risks and Impact Assessment
- Risks/threats: [unauthorized access, data minimization failure, purpose creep, profiling risk, transfer risk, children/minors risk].
- Likelihood: [low/medium/high]; Impact: [low/medium/high]; Risk rating matrix: [insert].
- POWR/State-specific equal employment or anti-discrimination considerations (if applicable): [insert].
7. Mitigations and Residual Risk
- Planned mitigations: [controls, timelines, owners].
- Testing/validation: [pen test, DPIA/ROPA updates, privacy-by-design checklist].
- Residual risk after mitigations: [rating]; decision: [accept/mitigate further/block].
8. Incident Response and Breach Notification
- Statute: RCW 19.255.010 (businesses); RCW 42.56.590 (state/local agencies). Originally enacted 2015; amended by HB 1071, effective March 1, 2020 (reduced timeline from 45 to 30 days + expanded PI definition).
- Timeline: Most expedient time possible and within 30 days after discovery of breach (reduced from 45 days in 2020).
- AG notification: If 500+ WA residents affected. Electronically via Data Breach Notification Web Form. Within 30 days of discovery. HIPAA/federal banking entities still must notify AG (even if exempt from consumer notice).
- State agencies: May delay up to additional 14 days to allow translation into primary language of affected resident.
- Private right of action: Allowed. Consumer injured by violation may institute civil action to recover damages.
- Enforcement: AG may bring action on behalf of state or residents. Violations = unfair or deceptive act + unfair method of competition.
- Triggers: Breach of security = unauthorized acquisition of PI. PI = first name/initial + last name + (SSN, DL/state ID, financial account + security/access code, biometric, username/email + password/security question, medical/health insurance, student/military ID, passport).
- Exception: Good-faith employee acquisition. Law enforcement delay permitted (must document reason). Encryption safe harbor.
- Coordination with other states/GLBA/HIPAA requirements if multi-state: [plan].
9. State Overlay Checklist (WA) - Breach Notification Only
- No comprehensive privacy law. Breach notification statute only (RCW 19.255.010 + RCW 42.56.590).
- Applicability: Persons/entities conducting business in WA + state/local agencies owning/licensing PI of WA residents.
- Sensitive data/Consumer rights: No mandated rights.
- Security: Reasonable security measures.
- Breach notice: 30 days (effective March 2020; reduced from 45). AG if 500+ (even HIPAA/banking entities). Private right of action. Unfair/deceptive practices enforcement. State agencies: +14 days for translation.
- Children: COPPA compliance.
- DPA/ROPA: Not required by law.
10. Approvals and Accountability
- Privacy lead/DPO review: [name/date].
- Security review: [name/date].
- Legal review (state law overlay): [name/date].
- Business owner certification: [name/date].
- Executive approver: [name/title/date].
11. Attachments
- Data flow diagrams/architecture.
- Records of processing activities entry.
- Vendor list and DPAs/SCCs.
- Legitimate interests assessment or risk assessment (if applicable).
- Testing summaries and pen test reports (if applicable).
- State-specific notices/links and breach templates.
Do more with Ezel
This free template is just the beginning. See how Ezel helps legal teams draft, research, and collaborate faster.
AI that drafts while you watch
Tell the AI what you need and watch your document transform in real-time. No more copy-pasting between tools or manually formatting changes.
- Natural language commands: "Add a force majeure clause"
- Context-aware suggestions based on document type
- Real-time streaming shows edits as they happen
- Milestone tracking and version comparison
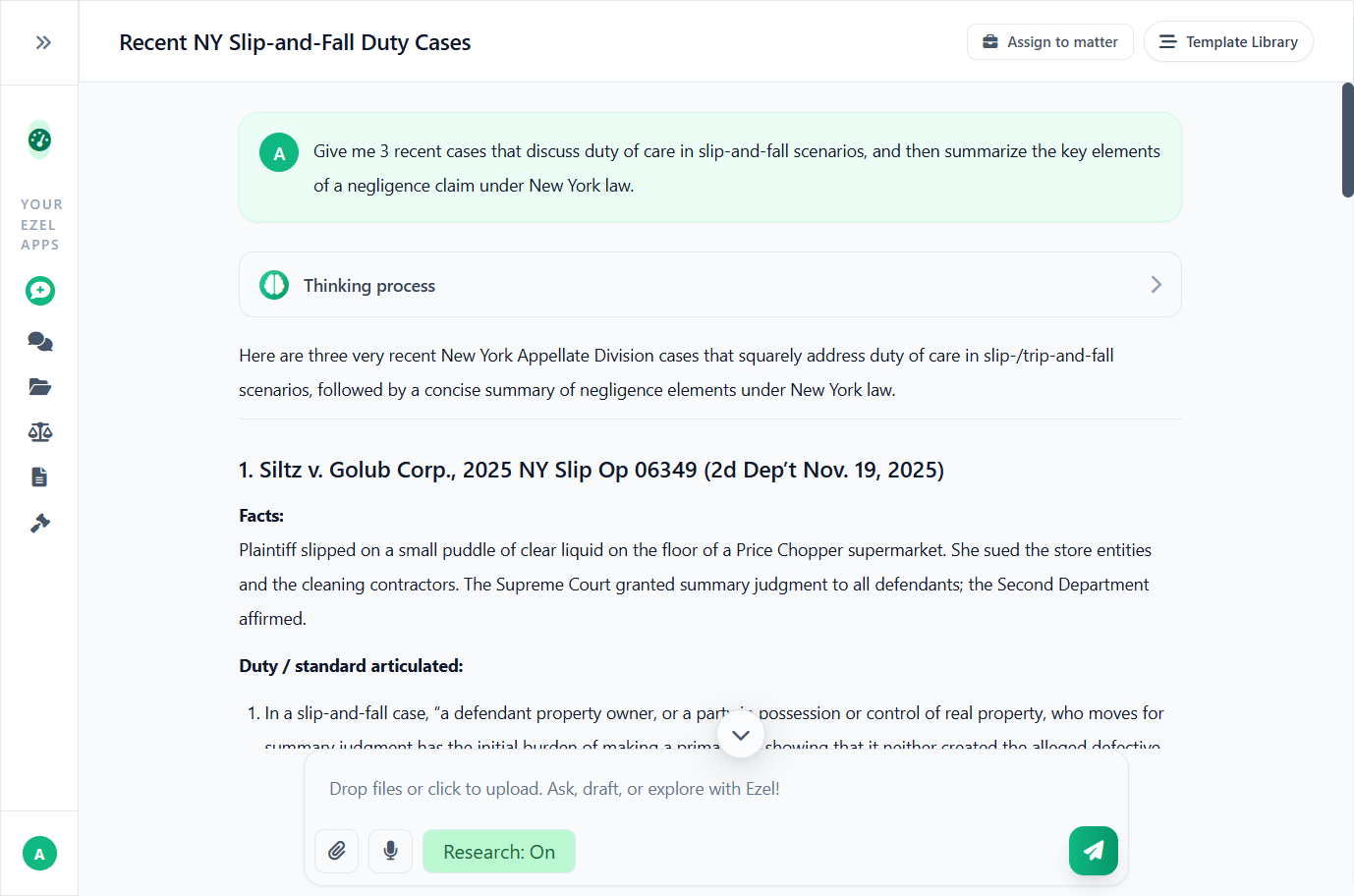
Research and draft in one conversation
Ask questions, attach documents, and get answers grounded in case law. Link chats to matters so the AI remembers your context.
- Pull statutes, case law, and secondary sources
- Attach and analyze contracts mid-conversation
- Link chats to matters for automatic context
- Your data never trains AI models
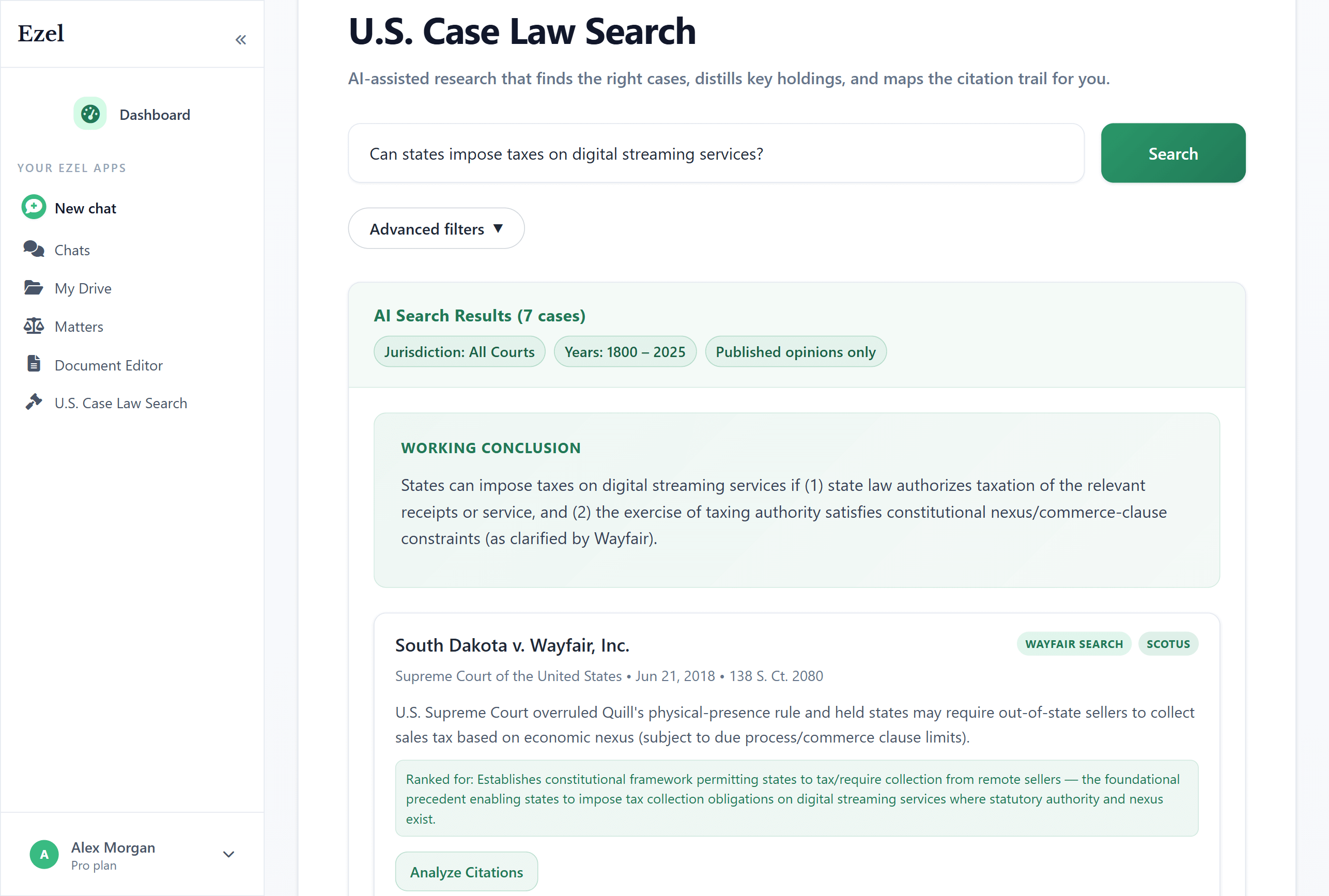
Search like you think
Describe your legal question in plain English. Filter by jurisdiction, date, and court level. Read full opinions without leaving Ezel.
- All 50 states plus federal courts
- Natural language queries - no boolean syntax
- Citation analysis and network exploration
- Copy quotes with automatic citation generation
Ready to transform your legal workflow?
Join legal teams using Ezel to draft documents, research case law, and organize matters — all in one workspace.