DATA PROCESSING ADDENDUM (SHORT FORM) — ALABAMA
DPA Effective Date: [__/__/____]
Master Agreement Reference: [________________________________] ("Master Agreement")
CONTROLLER (Covered Entity):
| Legal Name: | [________________________________] |
| Address: | [________________________________] |
| Contact Person: | [________________________________] |
| Email: | [________________________________] |
("Controller")
PROCESSOR (Third-Party Agent):
| Legal Name: | [________________________________] |
| Address: | [________________________________] |
| Contact Person: | [________________________________] |
| Email: | [________________________________] |
("Processor")
1. DEFINITIONS
1.1 "Applicable Alabama Laws" means the Alabama Data Breach Notification Act of 2018 (Ala. Code §§ 8-38-1 through 8-38-12) and any other Alabama state laws, regulations, or regulatory guidance relating to data protection, security, or privacy applicable to the Parties and the Processing.
1.2 "Covered Entity" means a person, sole proprietorship, partnership, government entity, corporation, nonprofit, trust, estate, cooperative association, or other business entity that acquires or uses sensitive personally identifying information (Ala. Code § 8-38-2(1)).
1.3 "Third-Party Agent" means an entity that has been contracted to maintain, store, process, or otherwise be permitted access to sensitive personally identifying information in connection with providing services to a covered entity (Ala. Code § 8-38-2(12)).
1.4 "Sensitive Personally Identifying Information" means an Alabama resident's first name or first initial and last name in combination with one or more of the following, when the data element is not encrypted, redacted, or otherwise rendered unusable: (a) a non-truncated Social Security number or tax identification number; (b) a non-truncated driver license number, state-issued identification card number, passport number, military identification number, or other unique identification number issued on a government document used to verify the identity of a specific individual; (c) a financial account number, including a bank account number, credit card number, or debit card number, in combination with any security code, access code, password, expiration date, or PIN that is necessary to access the financial account or to conduct a transaction that will credit or debit the financial account; (d) any information regarding an individual's medical history, mental or physical condition, or medical treatment or diagnosis by a health care professional; (e) an individual's health insurance policy number or subscriber identification number and any unique identifier used by a health insurer to identify the individual; (f) a user name or email address, in combination with a password or security question and answer that would permit access to an online account affiliated with the covered entity that is reasonably likely to contain or is used to obtain sensitive personally identifying information (Ala. Code § 8-38-2(8)).
1.5 "Breach of Security" (also "breach") means the unauthorized acquisition of data in electronic form containing sensitive personally identifying information; however, a breach of security does not include the good-faith acquisition of sensitive personally identifying information by an employee or agent of a covered entity or third-party agent, unless the information is used for a purpose unrelated to the business or subject to further unauthorized use (Ala. Code § 8-38-2(2)).
1.6 "Personal Information" means, for purposes of this DPA, any information that is linked or reasonably linkable to an identified or identifiable individual, including but not limited to Sensitive Personally Identifying Information.
1.7 "Processing" means any operation performed on Personal Information, including collection, recording, organization, storage, adaptation, retrieval, consultation, use, disclosure, dissemination, combination, restriction, erasure, or destruction.
1.8 "Sub-Processor" means any third party engaged by the Processor to perform Processing activities on behalf of the Controller.
2. SCOPE AND PURPOSE
2.1 This DPA applies to the Processing of Personal Information and Sensitive Personally Identifying Information by the Processor (acting as a Third-Party Agent under Alabama law) on behalf of the Controller (acting as a Covered Entity under Alabama law) in connection with the services provided under the Master Agreement.
2.2 The subject matter, nature, purpose, duration, types of data, and categories of data subjects are described in Annex A.
2.3 This DPA is incorporated into the Master Agreement. In case of conflict regarding data protection, this DPA prevails.
2.4 Although Alabama does not currently have a comprehensive consumer data privacy law granting individual access, deletion, correction, or portability rights, this DPA establishes contractual obligations for the secure processing of Personal Information and compliance with Alabama's breach notification requirements.
3. PROCESSOR OBLIGATIONS
The Processor shall:
3.1 Process Personal Information only in accordance with the Controller's documented instructions and this DPA.
3.2 Ensure that all personnel authorized to Process Personal Information have committed to confidentiality or are under statutory confidentiality obligations.
3.3 Implement and maintain reasonable security measures to protect Sensitive Personally Identifying Information against a breach of security, consistent with Ala. Code § 8-38-3.
3.4 Not sell, rent, release, disclose, disseminate, make available, or otherwise communicate Personal Information to any third party except as directed by the Controller or as required by law.
3.5 Not retain, use, or disclose Personal Information for any purpose other than the specific purposes set forth in this DPA and the Master Agreement.
3.6 Not combine Personal Information received from the Controller with Personal Information received from other sources, except as authorized by the Controller in writing.
3.7 Promptly notify the Controller if the Processor determines it can no longer meet its data security or confidentiality obligations.
3.8 Cooperate with the Controller in responding to any inquiries or investigations by the Alabama Attorney General or other regulators.
4. CONFIDENTIALITY
4.1 The Processor shall ensure that all personnel with access to Personal Information:
(a) Are informed of the confidential nature of the information;
(b) Have executed written confidentiality agreements or are under statutory confidentiality obligations;
(c) Have received training on data security and privacy requirements;
(d) Access Personal Information only as necessary to perform their duties.
4.2 Access to Personal Information shall be limited on a need-to-know basis.
5. PROCESSING INSTRUCTIONS
5.1 The Processor shall Process Personal Information only for the specific business purposes set forth in Annex A and the Master Agreement.
5.2 The Processor shall immediately inform the Controller if an instruction would, in the Processor's opinion, result in a violation of Applicable Alabama Laws.
5.3 The Processor shall not:
(a) Use Personal Information for its own purposes unrelated to the services provided to the Controller;
(b) Disclose Personal Information to third parties without the Controller's written authorization;
(c) Process Personal Information outside the scope of this DPA and the Master Agreement.
6. REASONABLE SECURITY MEASURES (Ala. Code § 8-38-3)
Pursuant to Ala. Code § 8-38-3, each covered entity and third-party agent shall implement and maintain reasonable security measures to protect Sensitive Personally Identifying Information against a breach of security. The Processor shall implement security measures that are "practicable for the covered entity or third-party agent to implement and maintain," which shall include:
6.1 Administrative Safeguards
☐ Designation of an employee or employees to coordinate the security program
☐ Identification of internal and external risks to the security, confidentiality, and integrity of Sensitive Personally Identifying Information
☐ Adoption of appropriate information safeguards to address identified risks and assess their effectiveness
☐ Regular training for employees on security practices and procedures
☐ Oversight of service providers and Sub-Processors to ensure they maintain appropriate safeguards
☐ Adjustment of the security program based on business changes or new circumstances
☐ Written information security policy
☐ Incident response plan
☐ Risk assessments conducted at least annually
6.2 Technical Safeguards
☐ Encryption of Sensitive Personally Identifying Information in transit (TLS 1.2+) and at rest (AES-256 or equivalent)
☐ Multi-factor authentication for access to systems containing Sensitive Personally Identifying Information
☐ Firewalls, intrusion detection/prevention systems, and network segmentation
☐ Regular vulnerability scanning and annual penetration testing
☐ Automated patch management
☐ Role-based access controls with least-privilege principles
☐ Data loss prevention tools
☐ Security event logging and monitoring (log retention: [____] months)
☐ Regular testing and monitoring of the effectiveness of key controls
6.3 Physical Safeguards
☐ Physical access controls to data processing and storage facilities
☐ Visitor management and logging
☐ Secure disposal of physical media containing Sensitive Personally Identifying Information
☐ Environmental controls (fire suppression, climate control, power backup)
☐ Protection against unauthorized access during collection, transportation, and disposal
6.4 Secure Disposal
☐ Erasing electronic media so that information cannot be read or reconstructed (consistent with NIST SP 800-88)
☐ Shredding of paper records containing Sensitive Personally Identifying Information
☐ Destruction of physical media beyond practical reconstruction
6.5 Detailed security measures are described in Annex B.
6.6 The Processor shall regularly test and update its security measures to address emerging threats and vulnerabilities.
6.7 Compliance Safe Harbor (Ala. Code § 8-38-9)
A covered entity or third-party agent that is in compliance with the security requirements of any of the following shall be deemed to be in compliance with the reasonable security measures required under § 8-38-3:
☐ Title V of the Gramm-Leach-Bliley Act (15 U.S.C. § 6801 et seq.)
☐ HIPAA and the HITECH Act
☐ Federal Information Security Modernization Act (FISMA)
☐ Other applicable federal or state regulatory requirements
Processor's Applicable Safe Harbor (if any): [________________________________]
7. DATA BREACH NOTIFICATION
7.1 Investigation of Breach (Ala. Code § 8-38-4)
Upon discovering a suspected breach or upon receiving notice of a breach from a third party, the Processor shall:
(a) Conduct a good faith and prompt investigation to determine the likelihood that Sensitive Personally Identifying Information has been or will be misused;
(b) Determine whether the breach is reasonably likely to cause substantial harm to the individuals to whom the information relates;
(c) Document the investigation and conclusions.
7.2 Third-Party Agent Notification to Covered Entity (Ala. Code § 8-38-7)
The Processor (as a Third-Party Agent) shall notify the Controller (as a Covered Entity) of any breach of security as expeditiously as possible and without unreasonable delay, but no later than ten (10) days following the Processor's determination that a breach has or is reasonably believed to have occurred, or upon notice from a third party that a breach has occurred.
7.3 Content of Notification
The Processor's notification to the Controller shall include, to the extent available:
(a) Description of the nature of the breach;
(b) Categories and approximate number of affected individuals;
(c) Types of Sensitive Personally Identifying Information compromised;
(d) Contact information for the Processor's incident response lead;
(e) Description of likely consequences;
(f) Measures taken or proposed to contain and remediate the breach;
(g) Date and time of discovery;
(h) Whether the affected data was encrypted.
7.4 Cooperation with Controller's Notification Obligations
The Processor shall cooperate with the Controller in fulfilling the Controller's notification obligations under Ala. Code § 8-38-5, including:
Individual Notification: The Controller must provide individual notification to each affected Alabama resident as expeditiously as possible and without unreasonable delay, but no later than forty-five (45) days from the date the entity determines that a breach has occurred.
Content of Individual Notification (Ala. Code § 8-38-5(b)): Notice shall include:
☐ The date, estimated date, or estimated date range of the breach
☐ A description of the Sensitive Personally Identifying Information that was acquired by the unauthorized person as part of the breach
☐ A general description of the actions taken by the entity to restore the security and confidentiality of the personal information involved in the breach
☐ A general description of the steps an affected individual can take to protect the individual, including information regarding how to place a credit freeze
☐ Contact information for the entity, including a toll-free telephone number, mailing address, and, if one exists, an email address
Attorney General Notification (Ala. Code § 8-38-6): If the breach affects more than 1,000 Alabama residents, the Controller must notify the Alabama Attorney General as expeditiously as possible and without unreasonable delay, and no later than 45 days from determination.
Consumer Reporting Agency Notification (Ala. Code § 8-38-6): If the breach affects more than 1,000 Alabama residents, the Controller must also notify consumer reporting agencies.
7.5 Evidence Preservation
The Processor shall preserve all evidence related to the breach and shall not alter, destroy, or conceal any evidence without the Controller's written consent.
7.6 Public Statements
The Processor shall not make any public statement regarding the breach without the Controller's prior written consent, unless required by law.
7.7 Penalties for Non-Compliance (Ala. Code § 8-38-11)
The Parties acknowledge that a covered entity that fails to comply with Alabama's breach notification requirements is subject to a civil penalty of not more than $5,000 per day for each consecutive day of noncompliance, with a maximum total penalty of $500,000 per breach.
8. SUB-PROCESSOR MANAGEMENT
8.1 The Processor shall not engage any Sub-Processor without:
☐ Option A: The Controller's prior specific written consent for each Sub-Processor
☐ Option B: The Controller's general written authorization with [____] days' prior notice and [____] days' objection period
8.2 Each Sub-Processor shall be bound by a written contract that:
(a) Imposes data security obligations no less protective than those in this DPA;
(b) Requires the Sub-Processor to implement and maintain reasonable security measures consistent with Ala. Code § 8-38-3;
(c) Requires breach notification to the Processor within [____] hours of discovery;
(d) Permits the Processor and Controller to audit the Sub-Processor's compliance.
8.3 The Processor shall remain fully liable for the acts and omissions of its Sub-Processors.
8.4 Approved Sub-Processors are listed in Annex C.
9. DATA SUBJECT RIGHTS ASSISTANCE
9.1 Alabama does not currently have a comprehensive consumer data privacy law that grants individual rights of access, deletion, correction, or portability. However, the Processor shall:
(a) Assist the Controller in responding to any consumer inquiries regarding their Personal Information;
(b) Cooperate with the Controller in fulfilling privacy rights obligations arising under other applicable laws (e.g., CCPA/CPRA for California residents, VCDPA for Virginia residents, TDPSA for Texas residents);
(c) Promptly forward to the Controller any requests received directly from individuals;
(d) Cooperate with the Controller in addressing any future Alabama privacy legislation that may be enacted.
9.2 If Alabama enacts comprehensive privacy legislation in the future, the Parties shall negotiate in good faith to amend this DPA to address any new requirements.
10. AUDIT RIGHTS
10.1 The Processor shall make available to the Controller all information necessary to demonstrate compliance with this DPA and Applicable Alabama Laws.
10.2 Audit options:
☐ Option A: Direct on-site or remote audit upon [____] days' notice, no more than [____] time(s) per year
☐ Option B: Annual third-party audit reports (SOC 2 Type II, ISO 27001), with additional direct audit rights if deficiencies or breach
☐ Option C: Combination
10.3 Full cooperation with audits; access to facilities, systems, personnel, and records.
10.4 Prompt remediation of identified deficiencies within [____] business days.
10.5 Audit costs: ☐ Controller ☐ Processor (if non-compliance found) ☐ Shared: [________________________________]
11. DATA RETURN AND DELETION
11.1 Upon expiration or termination of the Master Agreement, or upon the Controller's request, the Processor shall:
☐ Return all Personal Information to the Controller in a structured, machine-readable format; and/or
☐ Securely delete all Personal Information using methods rendering the data permanently unrecoverable (NIST SP 800-88 compliant)
11.2 Completion within [____] days of instruction or termination.
11.3 Written certification of return or deletion.
11.4 The Processor may retain Personal Information only as required by law, with continued DPA protections until secure deletion.
12. CROSS-BORDER DATA TRANSFERS
12.1 The Processor shall not transfer Personal Information outside the United States without the Controller's prior written authorization.
12.2 If authorized, appropriate safeguards shall include:
☐ Standard contractual clauses or data processing agreements
☐ Data Privacy Framework certification
☐ Equivalent contractual protections
☐ Other: [________________________________]
13. RECORD-KEEPING
13.1 The Processor shall maintain records of Processing activities, including:
(a) Categories of Processing carried out;
(b) Types of Personal Information processed;
(c) Security measures implemented;
(d) Any Data Breaches and remediation actions;
(e) Sub-Processor engagements.
13.2 Records shall be maintained for at least [____] years and made available to the Controller and regulators upon request.
14. FUTURE ALABAMA PRIVACY LEGISLATION
14.1 The Parties acknowledge that Alabama may enact comprehensive privacy legislation in the future.
14.2 The Processor agrees to monitor developments in Alabama privacy law and promptly notify the Controller of any new legislation or regulatory guidance that may affect the Processor's obligations under this DPA.
14.3 Upon enactment of new Alabama privacy legislation, the Parties shall negotiate in good faith to amend this DPA to incorporate any additional requirements within [____] days of the effective date of such legislation.
15. TERM AND TERMINATION
15.1 Effective on the DPA Effective Date; coterminous with the Master Agreement.
15.2 Either Party may terminate upon material breach not cured within [____] days of written notice.
15.3 Immediate termination if the Processor can no longer meet its Applicable Alabama Law obligations.
15.4 Sections 4, 6, 7, 11, and 16 survive termination.
16. LIABILITY AND INDEMNIFICATION
16.1 Liability.
☐ Subject to Master Agreement limitation of liability
☐ Separate cap: $[________________________________] or [____]x annual fees
☐ No cap for willful misconduct, gross negligence, or material breach of data security obligations
16.2 The Processor shall indemnify the Controller for claims arising from:
(a) The Processor's breach of this DPA;
(b) The Processor's violation of Applicable Alabama Laws;
(c) Any Data Breach caused by the Processor's failure to implement and maintain reasonable security measures;
(d) Penalties imposed by the Alabama Attorney General arising from the Processor's failure to comply with breach notification obligations.
16.3 The Controller shall indemnify the Processor for claims arising from the Controller's breach of this DPA, except to the extent caused by the Processor's fault.
16.4 The Parties acknowledge that the Alabama Attorney General has enforcement authority under Ala. Code § 8-38-10, and that violations may result in civil penalties of up to $5,000 per day, with a maximum of $500,000 per breach (Ala. Code § 8-38-11).
17. GENERAL PROVISIONS
17.1 Governing Law. This DPA shall be governed by the laws of the State of Alabama, without regard to conflict of laws principles.
17.2 Forum. Any dispute shall be resolved in the state or federal courts located in [________________________________] County, Alabama.
17.3 Amendments. Amendments require written agreement signed by both Parties.
17.4 Severability. Invalid provisions shall not affect the remainder.
17.5 Order of Precedence. (1) Applicable Alabama Laws; (2) this DPA; (3) Master Agreement.
17.6 Entire Agreement. This DPA, together with the Master Agreement and annexes, constitutes the entire agreement regarding data protection.
18. SIGNATURES
CONTROLLER (Covered Entity):
| Signature: | [________________________________] |
| Printed Name: | [________________________________] |
| Title: | [________________________________] |
| Date: | [__/__/____] |
PROCESSOR (Third-Party Agent):
| Signature: | [________________________________] |
| Printed Name: | [________________________________] |
| Title: | [________________________________] |
| Date: | [__/__/____] |
ANNEX A — DATA PROCESSING DESCRIPTION
| Field | Description |
|---|---|
| Subject Matter: | [________________________________] |
| Duration: | [________________________________] |
| Nature and Purpose: | [________________________________] |
| Types of Personal Information: | [________________________________] |
| Types of Sensitive Personally Identifying Information: | [________________________________] |
| Categories of Data Subjects: | [________________________________] |
| Frequency of Transfer: | [________________________________] |
| Retention Period: | [________________________________] |
ANNEX B — TECHNICAL AND ORGANIZATIONAL SECURITY MEASURES
| Measure | Description | Status |
|---|---|---|
| Encryption — Transit | TLS 1.2+ | ☐ Implemented |
| Encryption — At Rest | AES-256 or equivalent | ☐ Implemented |
| Access Control | Role-based; least-privilege | ☐ Implemented |
| MFA | For all access to SPII systems | ☐ Implemented |
| Network Security | Firewalls, IDS/IPS, segmentation | ☐ Implemented |
| Vulnerability Management | Scanning; pen testing | ☐ Implemented |
| Logging/Monitoring | SIEM; log retention [____] months | ☐ Implemented |
| DLP | Data loss prevention | ☐ Implemented |
| BCP/DR | Plans tested regularly | ☐ Implemented |
| Physical Security | Access controls; environmental controls | ☐ Implemented |
| Employee Security | Background checks; NDAs; training | ☐ Implemented |
| Incident Response | Documented plan; response team | ☐ Implemented |
| Secure Disposal | NIST SP 800-88; shredding | ☐ Implemented |
| Other: | [________________________________] | ☐ Implemented |
ANNEX C — APPROVED SUB-PROCESSOR LIST
| Sub-Processor Name | Processing Activities | Location | Date Approved |
|---|---|---|---|
| [________________________________] | [________________________________] | [________________________________] | [__/__/____] |
| [________________________________] | [________________________________] | [________________________________] | [__/__/____] |
| [________________________________] | [________________________________] | [________________________________] | [__/__/____] |
This template is provided by ezel.ai for informational purposes only and does not constitute legal advice. Consult qualified Alabama counsel before executing this DPA.
Do more with Ezel
This free template is just the beginning. See how Ezel helps legal teams draft, research, and collaborate faster.
AI that drafts while you watch
Tell the AI what you need and watch your document transform in real-time. No more copy-pasting between tools or manually formatting changes.
- Natural language commands: "Add a force majeure clause"
- Context-aware suggestions based on document type
- Real-time streaming shows edits as they happen
- Milestone tracking and version comparison
Research and draft in one conversation
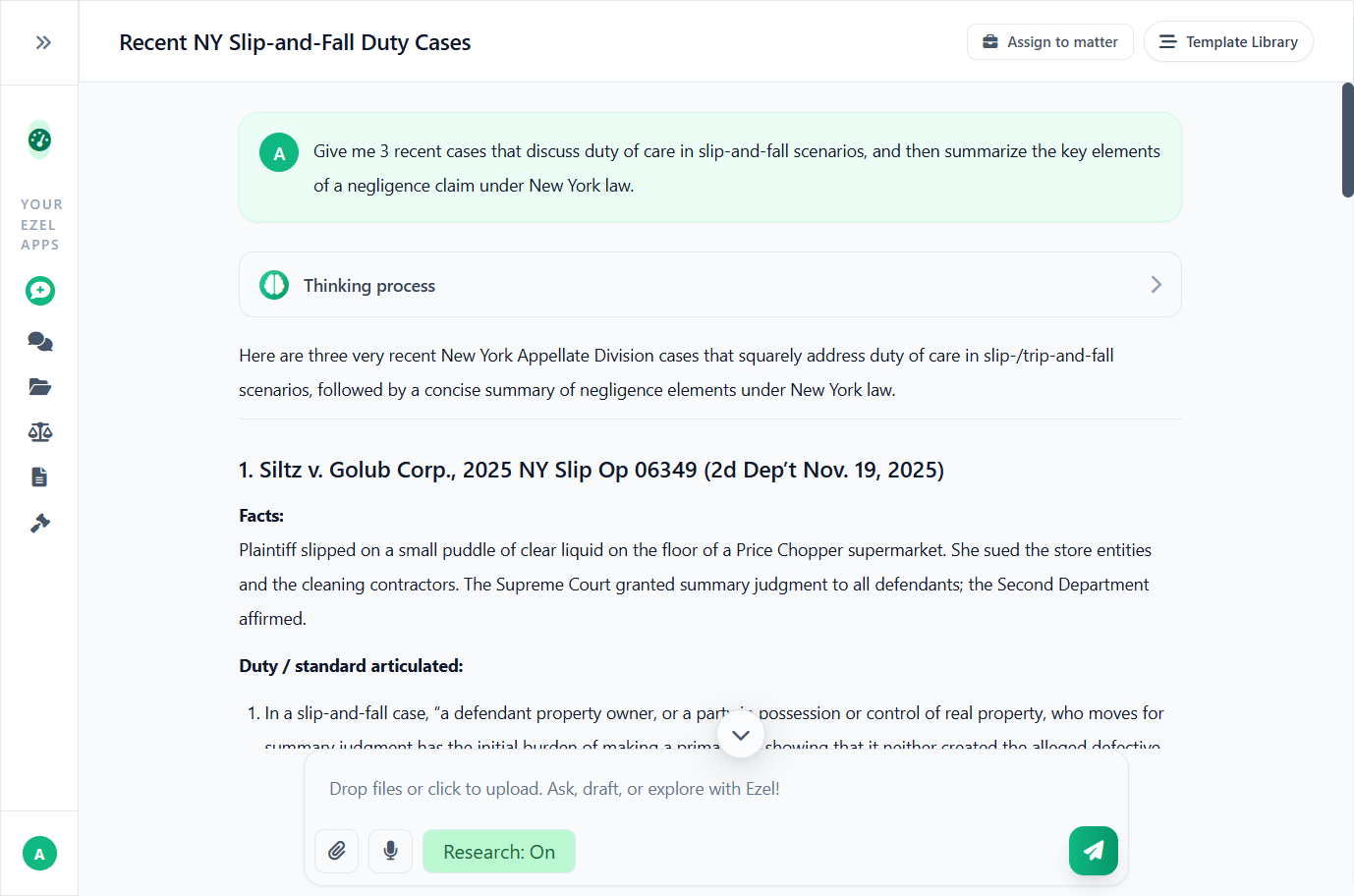
Ask questions, attach documents, and get answers grounded in case law. Link chats to matters so the AI remembers your context.
- Pull statutes, case law, and secondary sources
- Attach and analyze contracts mid-conversation
- Link chats to matters for automatic context
- Your data never trains AI models
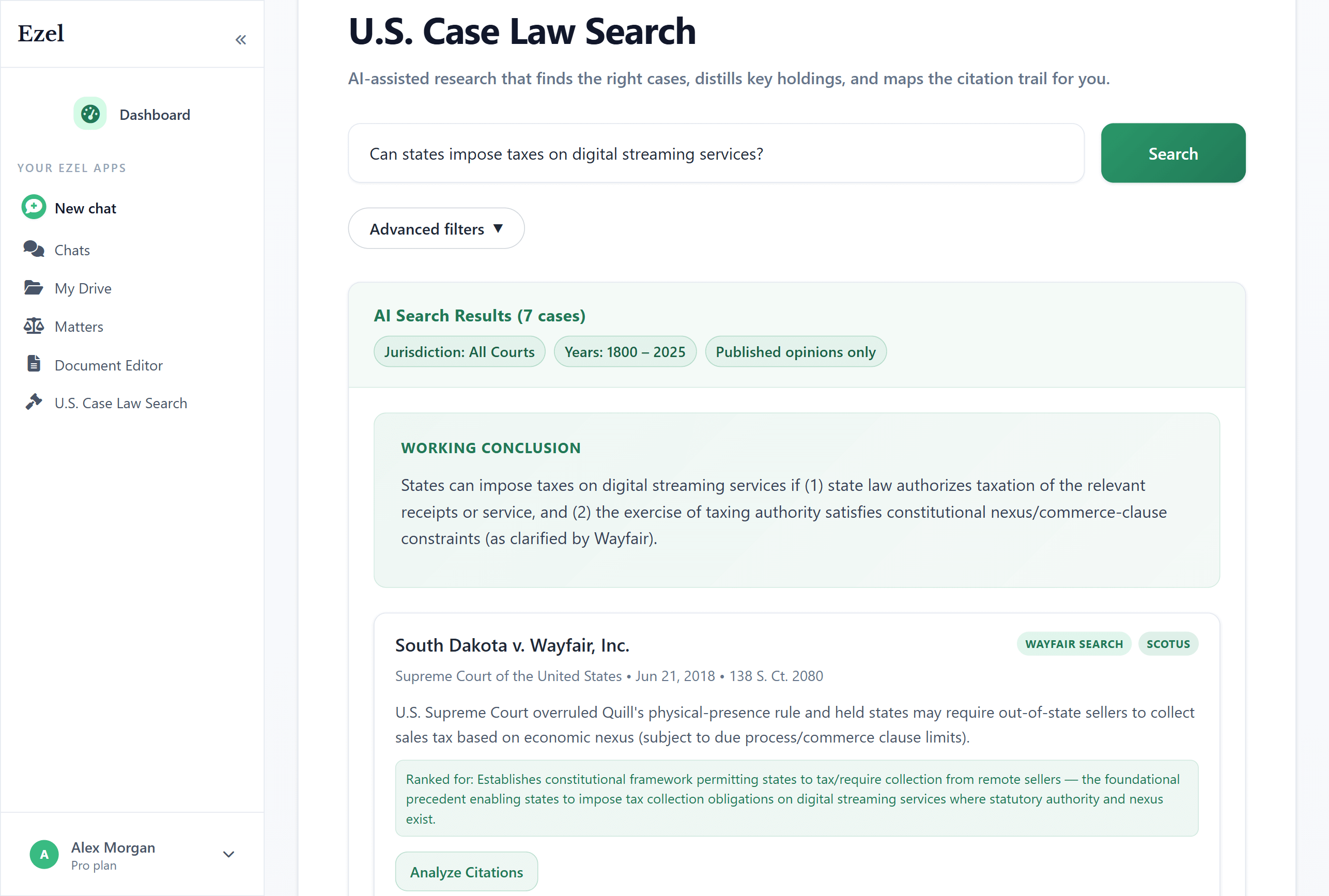
Search like you think
Describe your legal question in plain English. Filter by jurisdiction, date, and court level. Read full opinions without leaving Ezel.
- All 50 states plus federal courts
- Natural language queries - no boolean syntax
- Citation analysis and network exploration
- Copy quotes with automatic citation generation
Ready to transform your legal workflow?
Join legal teams using Ezel to draft documents, research case law, and organize matters — all in one workspace.