DATA PROCESSING ADDENDUM (COMPREHENSIVE) - NEW YORK
TABLE OF CONTENTS
- Roles and Scope
- Duration and Instructions
- Nature, Purpose, Types of Data, and Categories of Data Subjects
- Provider Obligations (Processor)
- Anonymization and Aggregation (if applicable)
- Subprocessing
- Security Measures
- Data Residency and Localization
- Personal Data Breach
- Data Subject Requests
- Return and Deletion
- Audits and Certifications
- Cross-Border Transfers
- US State Privacy (New York and others)
- Liability and Indemnities
- Conflict; Order of Precedence
- Annexes (Security Controls; SCC/UK Addendum; Completion Guidance)
- Signatures
1. ROLES AND SCOPE
- Parties: [CONTROLLER/PROCESSOR] roles for each party.
- Default: Provider acts as Processor (or Subprocessor) on behalf of Customer for Personal Data described herein.
- Optional: For Controller-to-Controller or joint-controller arrangements, select SCC Module 1 or Module 4 and document responsibilities in Annex I.
- Subject matter and purpose: provision of [SERVICES] under the [MASTER AGREEMENT NAME/DATE].
- DPO or Privacy Contact (if applicable): [NAME/EMAIL] for each party.
2. DURATION AND INSTRUCTIONS
- Processing duration: through the term of the underlying agreement plus wind-down.
- Provider will process Personal Data only on documented instructions from Customer, including regarding transfers; Provider will notify Customer if instructions conflict with Applicable Law.
3. NATURE, PURPOSE, TYPES OF DATA, AND CATEGORIES OF DATA SUBJECTS
- Nature and purpose: [e.g., hosting, support, analytics].
- Types of Personal Data: [contact info, device IDs, usage data, HR data, etc.].
- Data Subjects: [customers, employees, contractors, end users].
- Sensitive or Special Categories (if any): [health, biometric, racial/ethnic, political, etc.] require prior written approval and enhanced safeguards (encryption in transit/at rest, access restriction, need-to-know, DPIA/TIA if applicable). If none, state "Not processed."
4. PROVIDER OBLIGATIONS (PROCESSOR)
- Maintain confidentiality for personnel; background checks where appropriate.
- Process only per instructions; assist with impact assessments and consultations with authorities when required.
- Maintain records of processing as required by law.
5. ANONYMIZATION AND AGGREGATION (IF APPLICABLE)
- Provider may [choose: (a) not use / (b) use] Customer Personal Data to create de-identified or aggregated data for [benchmarking/product improvement/security analytics] provided it: (i) is irreversibly de-identified, (ii) contains no Personal Data, (iii) is not used to re-identify any individual or Customer, and (iv) complies with Applicable Law. If prohibited, state "No de-identified/aggregated use permitted."
6. SUBPROCESSING
- Authorized subprocessors listed in Annex; advance notice of new subprocessors; Customer objection rights within [X] days for reasonable, documented grounds.
- Provider remains liable for subprocessors; flow-down of equivalent obligations.
7. SECURITY MEASURES
- Implement technical and organizational measures appropriate to risk (see Annex 1).
- Access controls, encryption, logging and monitoring, vulnerability management, backup and disaster recovery, secure development, segregation of environments, personnel training.
8. DATA RESIDENCY AND LOCALIZATION
- Primary storage or processing locations: [LIST REGIONS/COUNTRIES].
- Customer options (if offered): [EEA-only/US-only/regional ringfencing]; any change requires prior written notice and, if applicable, updated transfer mechanism and TIA.
9. PERSONAL DATA BREACH
- Notify Customer without undue delay and within [X] hours of confirmation.
- Include details: nature of breach, data types, data subjects affected, measures taken or proposed.
- Cooperate on notifications and remediation.
10. DATA SUBJECT REQUESTS
- Assist Customer in responding to DSRs (access, deletion, correction, portability, restriction) within applicable timelines.
- No responses directly to Data Subjects unless authorized or required by law (with notice to Customer).
11. RETURN AND DELETION
- Upon termination or expiration, delete or return Personal Data per Customer's choice, subject to legal retention obligations; certify completion on request.
12. AUDITS AND CERTIFICATIONS
- Provide SOC/ISO or equivalent reports where available; otherwise allow audits once annually with reasonable notice, subject to confidentiality and time/materials fees if on-site.
- Promptly address material findings.
13. CROSS-BORDER TRANSFERS
- If transferring from EEA/UK/Switzerland, incorporate SCCs: [Select Module 2 (Controller-Processor) or 3 (Processor-Processor)], with Annexes completed.
- UK transfers: attach UK Addendum or IDTA with selected options.
- Conduct Transfer Impact Assessments (TIAs) as required; implement additional measures (encryption, pseudonymization, access controls) if indicated by TIA outcomes.
14. US STATE PRIVACY (NEW YORK AND OTHERS)
- Provider acts as a "Service Provider" or "Processor" and shall not sell or share Personal Data, retain, use, or disclose Personal Data outside the scope of the Services, or combine Personal Data except as permitted by Applicable Law.
- Comply with the New York SHIELD Act data security requirements (reasonable administrative, technical, and physical safeguards), as applicable.
- If Provider is subject to New York Department of Financial Services cybersecurity rules (23 NYCRR 500), Provider will maintain compliance to the extent applicable to the Services.
- For other applicable US state privacy laws, Provider will act as a processor or service provider and provide reasonable assistance with consumer rights requests.
15. LIABILITY AND INDEMNITIES
- Liability and caps align with the master agreement; no cap circumvention unless specifically carved out.
- Breach of DPA confidentiality or security obligations may be a carve-out where negotiated.
16. CONFLICT; ORDER OF PRECEDENCE
- This DPA prevails over conflicting terms in the master agreement regarding data protection and security; otherwise, the master agreement controls.
17. ANNEXES
- Annex 1: Technical and Organizational Measures (TOMs). [Guidance: list access controls, encryption standards, network security, logging/monitoring, vulnerability management, backup/DR, secure SDLC, HR security, physical security.]
- Annex 2: Subprocessor list. [Guidance: name, service, location, data types, role.]
- Annex 3: SCCs details (Modules, Clauses, Annex I/II/III) and UK Addendum selections. [Guidance: complete data exporter/importer details, description of transfers, TOMs, and jurisdiction-specific options.]
18. SIGNATURES
Customer:
By: _________________________
Name: _______________________
Title: ________________________
Date: ________________________
Provider:
By: _________________________
Name: _______________________
Title: ________________________
Date: ________________________
Do more with Ezel
This free template is just the beginning. See how Ezel helps legal teams draft, research, and collaborate faster.
AI that drafts while you watch
Tell the AI what you need and watch your document transform in real-time. No more copy-pasting between tools or manually formatting changes.
- Natural language commands: "Add a force majeure clause"
- Context-aware suggestions based on document type
- Real-time streaming shows edits as they happen
- Milestone tracking and version comparison
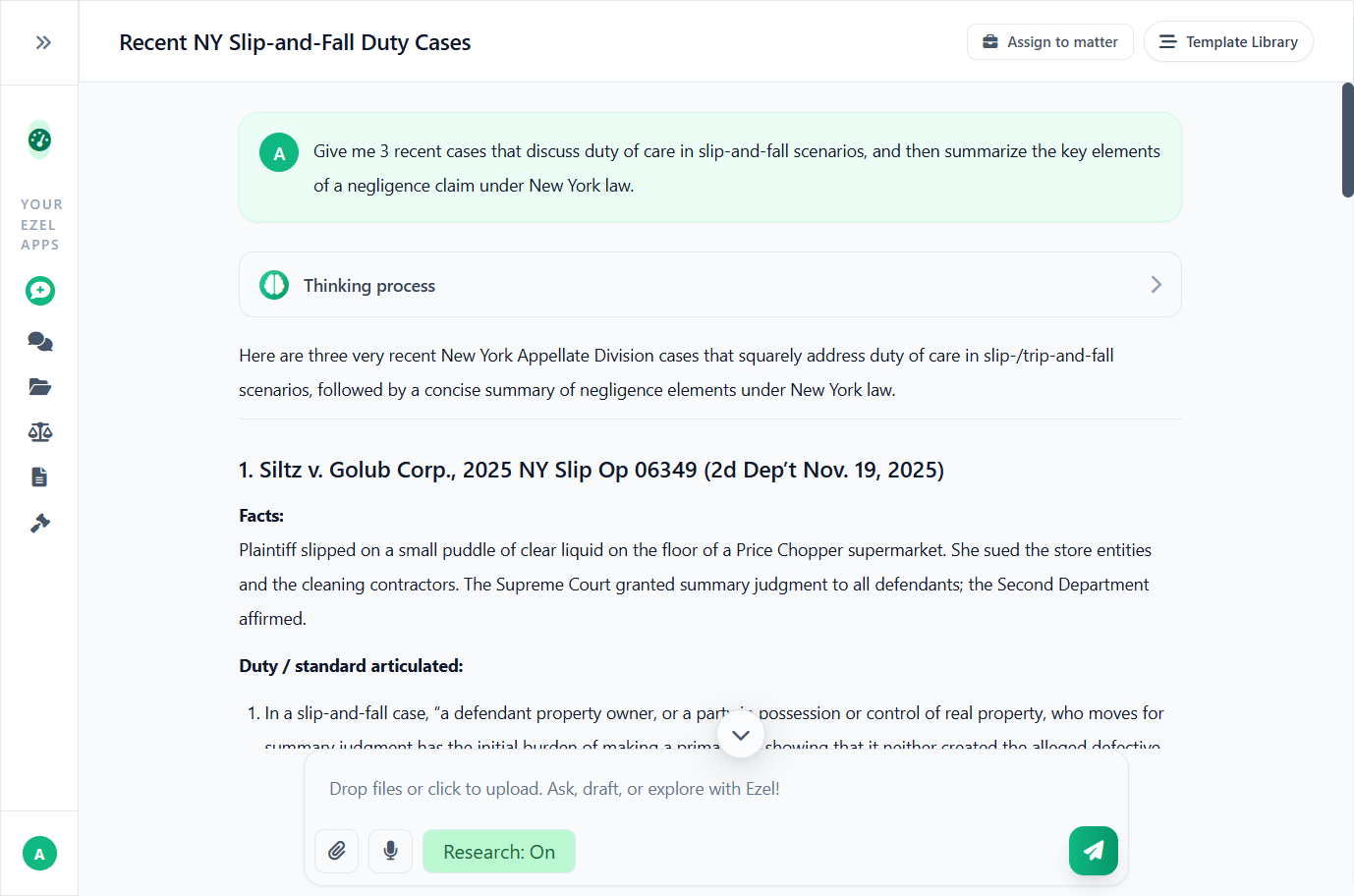
Research and draft in one conversation
Ask questions, attach documents, and get answers grounded in case law. Link chats to matters so the AI remembers your context.
- Pull statutes, case law, and secondary sources
- Attach and analyze contracts mid-conversation
- Link chats to matters for automatic context
- Your data never trains AI models
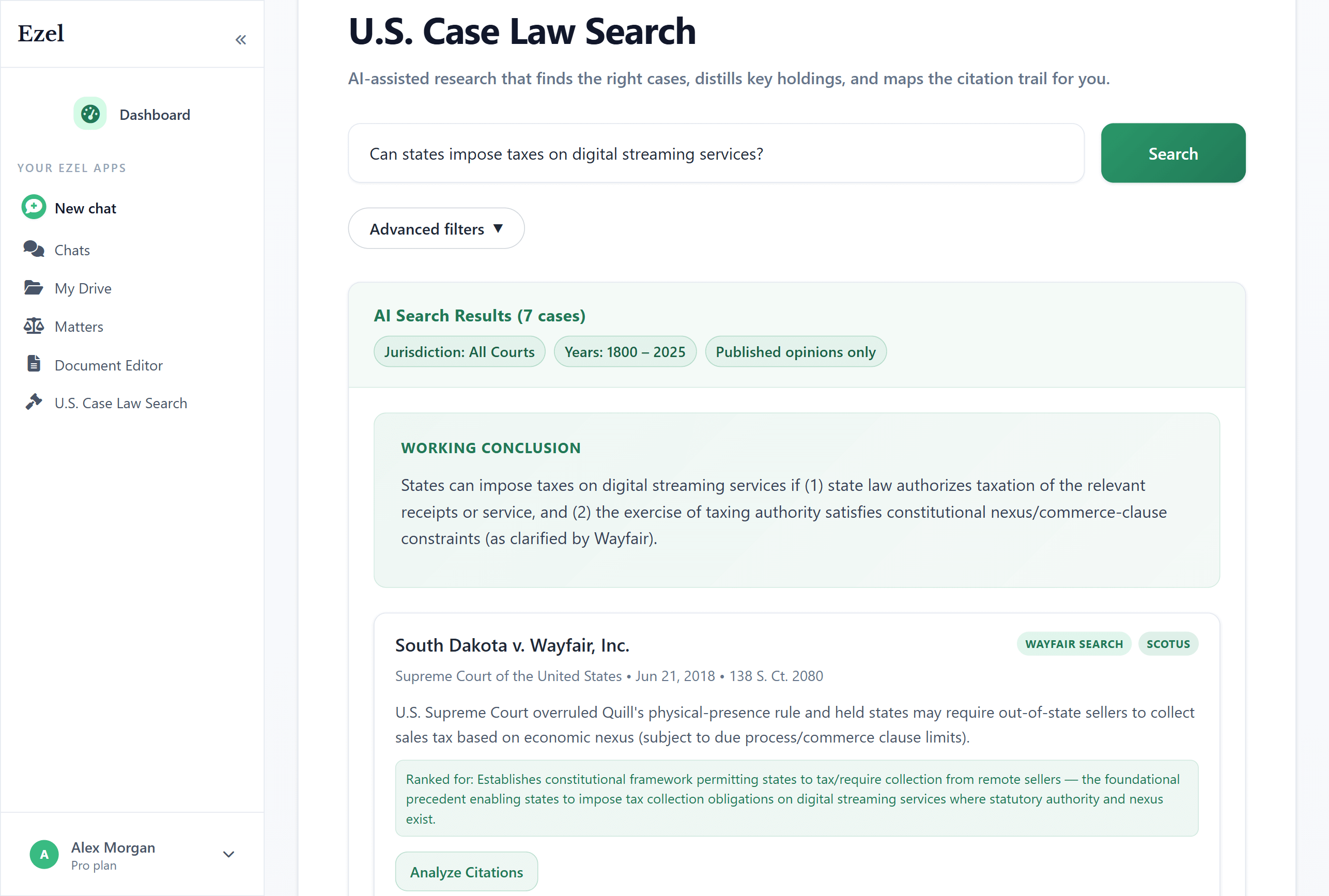
Search like you think
Describe your legal question in plain English. Filter by jurisdiction, date, and court level. Read full opinions without leaving Ezel.
- All 50 states plus federal courts
- Natural language queries - no boolean syntax
- Citation analysis and network exploration
- Copy quotes with automatic citation generation
Ready to transform your legal workflow?
Join legal teams using Ezel to draft documents, research case law, and organize matters — all in one workspace.